Your One Place to See and Act on Risk Across the Organization
Most orgs don’t lack findings. They lack a single, reliable place to decide what to fix next.
AI-powered engineering teams ship across dozens, sometimes hundreds, of repositories. Findings show up in Code Review Agent results, DeepScan Agent reports, tickets, and spreadsheets. The results are predictable as triage becomes fragmented and it gets harder to answer the questions leaders actually need to prioritize security work.
This is why we built the Risk Register.
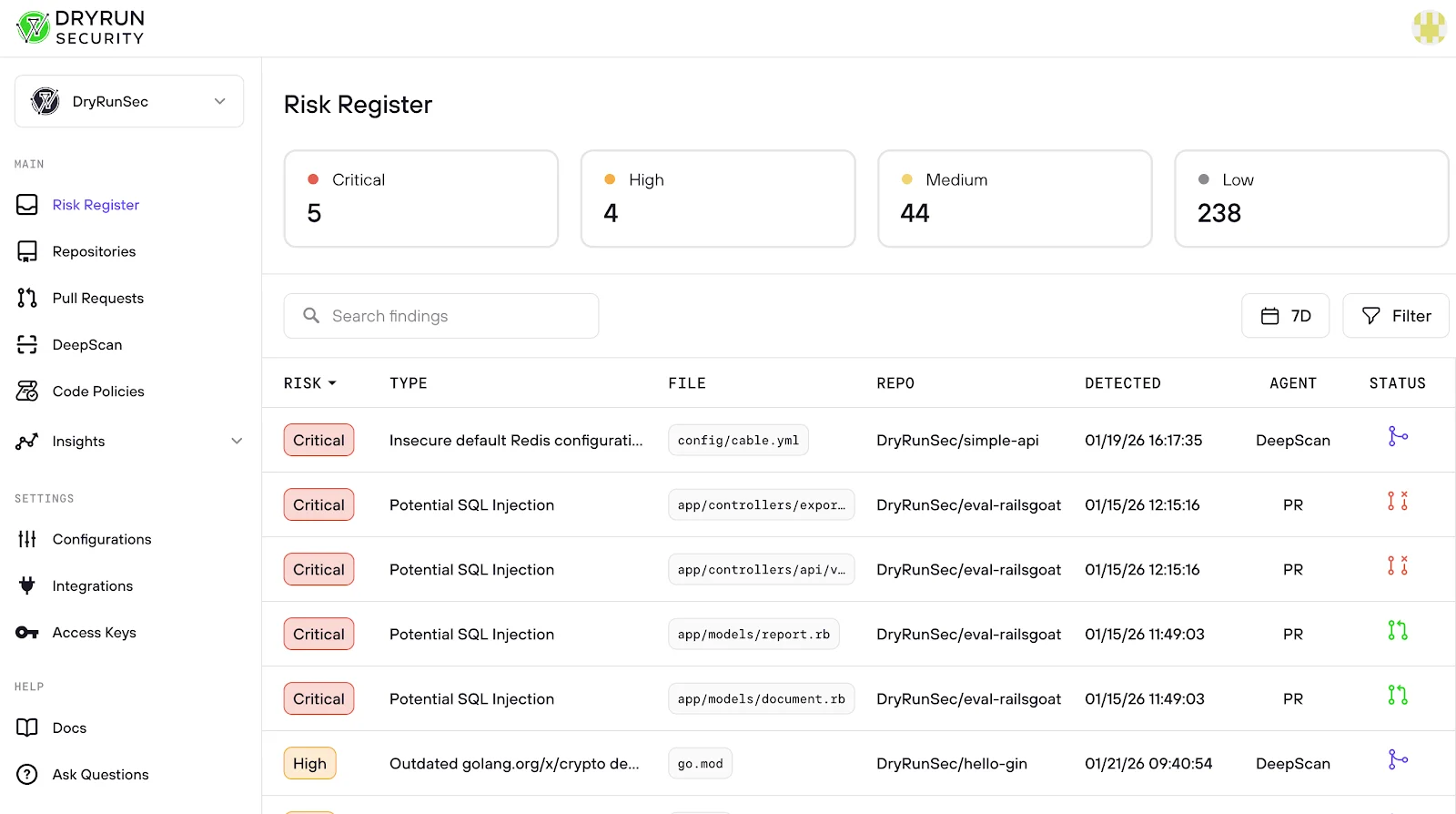
Risk Register is a new tool in the DryRun Security dashboard that centralizes findings from the Code Review Agent and the DeepScan Agent into one organization-wide view. It gives AppSec, DevSecOps, and engineering leaders a clear starting point to understand where risk lives, prioritize Critical and High issues, and drive the next right actions.
A clear starting point for AppSec, DevSecOps, and engineering leaders
DryRun Security agents help teams reduce risk in two key moments:
Code Review Agent in your pull requests: AI-native PR security that understands your code and intent, flags risky changes before they merge, and keeps developers moving with low-noise feedback powered by Contextual Security Analysis.
DeepScan Agent across your code repos: A deep, repository-wide assessment that surfaces the highest-risk issues beyond a single PR by reasoning across the codebase and filtering out junk findings.
Risk Register brings those worlds together. Instead of hopping between PRs and separate scan views, you get one place to track, understand, and prioritize risk across the entire organization.
With Risk Register, you can:
- See priority findings from the Code Review Agent and DeepScan Agent in one unified table
- Understand where risk concentrates by repository, type, and severity
- Move from org-level insight to an actionable list in seconds with filters and search
- Start with Critical and High, then drill down to the exact repo, file, and finding
Security work cannot live only in PRs
Working PR by PR can feel productive, but it leaves gaps. It is hard to maintain a true organization-wide picture of risk when your workflow is bound to whatever PR happens to be open.
Risk Register is built for the bigger, recurring needs of security and engineering leadership:
- Identifying which repositories carry the most high-severity risk
- Tracking whether Critical and High issues are trending in the right direction
- Spotting patterns emerging across the organization, not just in one repo or one PR
- Keeping triage focused on the work that reduces risk fastest
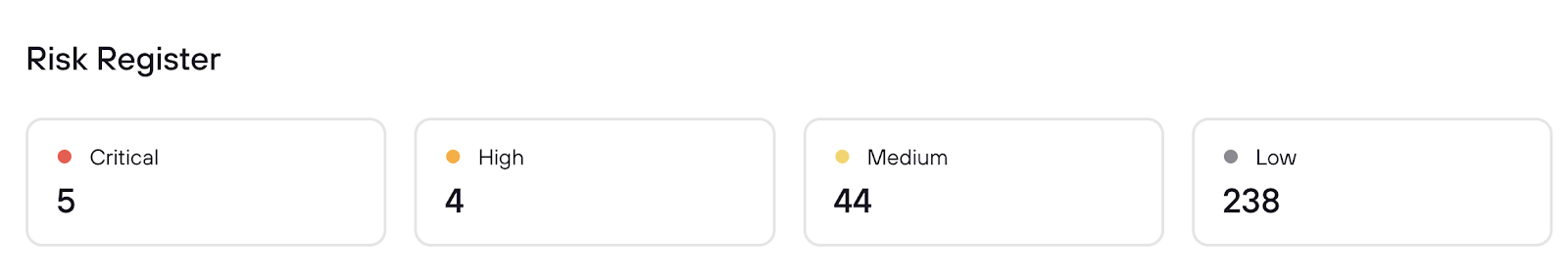
Criticality summary
Risk Register exposes your overall risk posture at a glance, including how many issues you have at each severity across Code Review Agent findings and DeepScan Agent findings.
Risk Register includes:
- Unified findings table across all repositories for the Code Review Agent and DeepScan Agent results
- Search to instantly locate findings by file, repo, or keyword
- Sortable Risk column
- Industry-standard severities: Critical, High, Medium, Low
- Severity model
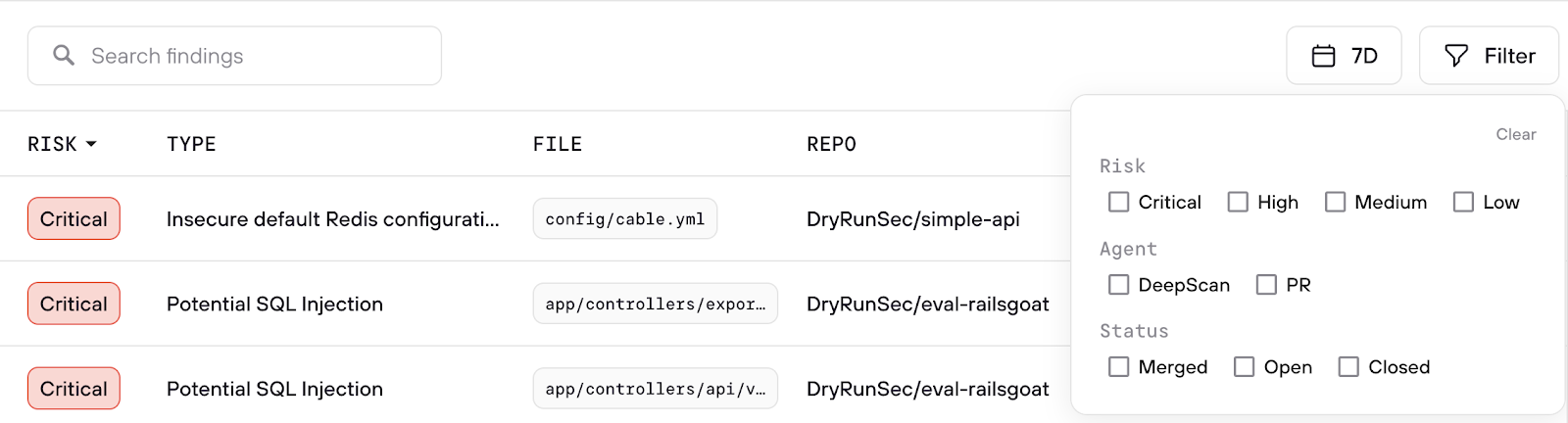
- Filters to focus the view:
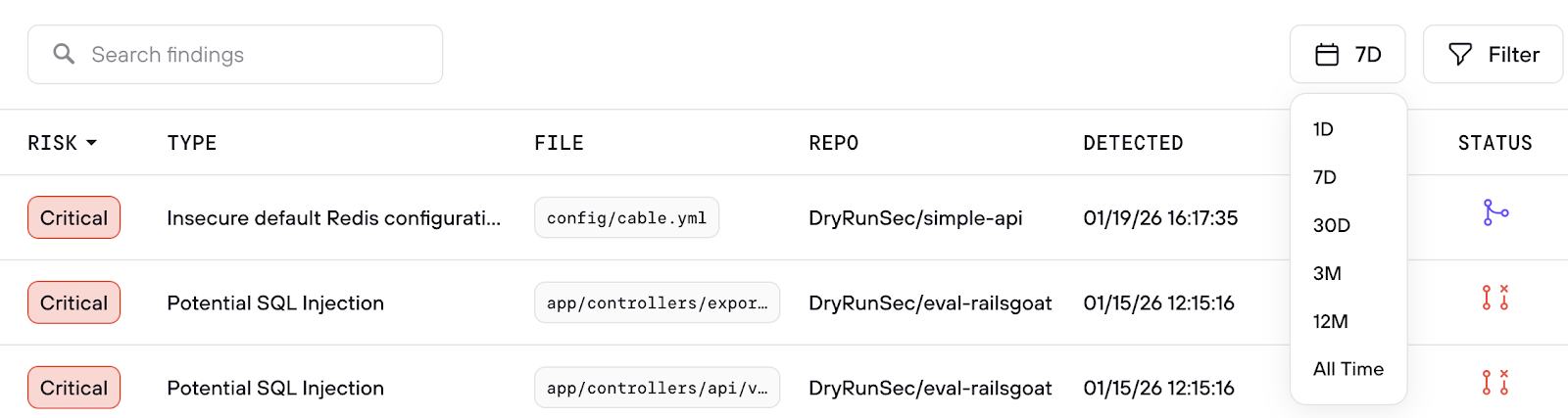
- Date ranges
- Risk level (Critical, High, Medium, Low)
- Agent (DeepScan Agent, Code Review Agent)
- Status (Merged, Open, Closed)
DryRun Security normalizes findings to industry-standard severities so teams can prioritize consistently across agents and repositories.
- Code Review Agent: mapping aligns closely to Fail → Critical, Risky → High, Info → Low
- DeepScan Agent and other analyzers: normalized to the same four-level model
- Configuration-aware: final severity reflects your analyzer setup in Default or Custom Configs
Filters to quickly find the most relevant risk
Filters to quickly find the most relevant risk
Designed for action, not just detection
Most security tools stop at detection. They generate findings and leave teams to figure out where risk is concentrated, what to fix first, and how it all adds up across the organization.
DryRun Security is built around action. That means context-rich findings, a consistent severity model, and a clear path from detection to decision.
Risk Register extends that philosophy beyond individual pull requests. It gives security and engineering leaders a shared, organization-wide view of risk, without forcing them to stitch together PRs, scans, and spreadsheets. By normalizing findings and reducing noise, it keeps attention focused on the work that actually reduces risk.
Instead of asking “what did we find,” teams can answer the more important question: “what should we fix next?”
Ready to see Risk Register in action?
Open it now: DryRun Security Dashboard → Risk Register
Want a walkthrough of how teams use it to prioritize risk across the organization? Request a demo.