The hardest problems in application security today are context-dependent. Authorization issues, PII data leaks, YAML mis-configurations in prod. Where code is run, why it was written, and what purpose it serves all make a huge difference in how much risk is being introduced to your codebase.
Natural Language Code Policies (NLCPs) let you phrase a security rule exactly the way you’d say it in a design review—“Does this endpoint require admin rights?”—and have DryRun enforce that rule every time a developer opens a pull request. Instead of guessing with brittle regular expressions, our Contextual Security Analysis engine translates plain-English rules into precise, always-up-to-date checks.
Here are three examples:
1. Authorization Gaps in a Rails Admin Controller
Customer policy: “If this is a new API endpoint, does it have proper authorization?”
A fintech customer relies on the Pundit gem for role‑based access control. When they added a new admin controller, DryRun Security flagged the pull request because the action skipped authorize entirely:
# app/controllers/admin/sso_controller.rb
class Admin::SsoController < ApplicationController
include Pundit::Authorization # Pundit wired in globally
def add_client_secret
# 🚩 missing `authorize`
secret = params[:secret]
ClientSecret.create!(secret: secret)
render json: { status: 'ok' }
end
end
DryRun Security finding:
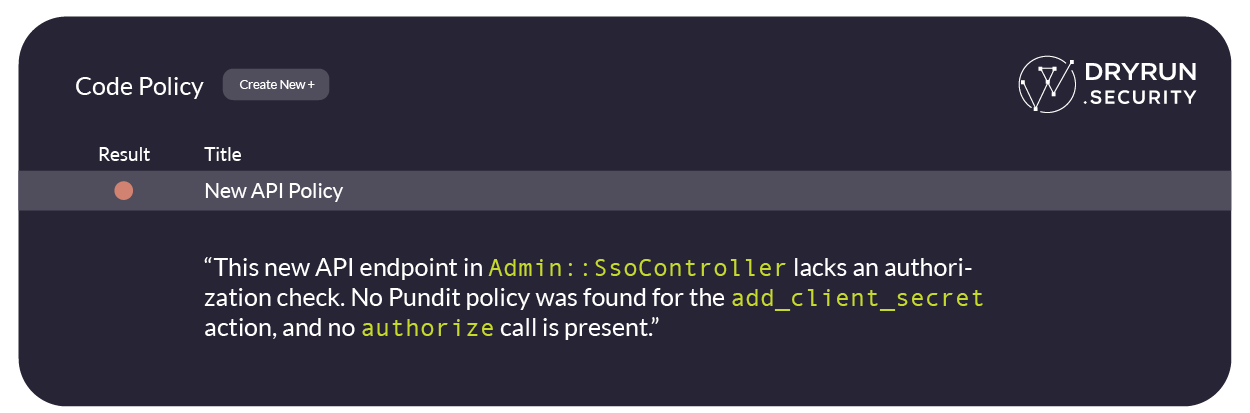
Because the policy triggered during the code review, the team fixed the issue before it reached staging, avoiding a bug‑bounty payout and reinforcing the habit of always calling authorize.
2. Hidden Landmines in GitHub Actions and IaC
Customer policy: “Does this change pose any security risk to GitHub Actions config?”
YAML pipelines are code, and misconfigurations can quietly grant attackers broad privileges. After a SaaS team tweaked its deployment workflow, DryRun Security produced this assessment:

A fragment of the workflow reveals the problems:
jobs:
deploy:
runs-on: ubuntu-latest
steps:
- name: Deploy
run: |
echo "Deploying ${{ github.event.inputs.tag }}" # unsanitized
aws s3 cp build.zip s3://$BUCKET/ --profile $AWS_PROFILE
--- REDACTED ---
One plain‑English policy caught four distinct vulnerability classes. Refactoring the YAML took minutes; cleaning up leaked credentials in production would have taken days.
3. Preventing PII from Sneaking into Logs
Customer policy: “Is any sensitive data, including personally identifiable information (PII), being sent to logs?”
While debugging a flaky test suite, an e‑commerce team started dumping full user states, including emails, into CSV files that were later uploaded to CI logs. DryRun intervened:

The developers moved the artifacts to a private S3 bucket and scrubbed PII before log emission. The fix took less than an hour. A breach notification would have taken weeks.
Why NLCPs Beat Pattern Matching
New to NLCPs? Start with the launch announcement or download the ready‑to‑go NLCP Starter Pack.
Pattern‑matching rules treat code as plain text. NLCPs treat code as context—tracking function calls, data flow, and configuration to decide whether a change is safe. That means fewer false positives, faster feedback, and problems discovered when the cost of change is lowest.
Try It Yourself
- Check out the NLCP Starter Pack.
- Drop a policy file into your repository.
- Push a branch and watch DryRun Security surface meaningful findings right in the review.
Context beats patterns—commit after commit.


